MISP 2025 Retrospective: Monthly Highlights & Workflow Improvements
As 2025 wraps up, we at Cosive are reflecting on the fantastic additions made to the MISP threat intelligence sharing platform over the past year.
The transition to the 2.5 branch has delivered a major UI/UX overhaul and modernised background processing that together boosted the platform’s performance.
It’s been a busy year – the incredibly active MISP developer community put out a dozen-plus releases in 2025 – and the results speak for themselves in new features and quality-of-life improvements for threat intel teams.
Below we recap some of the highlights from 2025, and extend a big thank you to the MISP core team and community for their hard work keeping this critical open-source tool moving forward.
Meanwhile, if you're running an outdated version of MISP, we can help get you back in sync with the latest version. CloudMISP is our MISP as a service offering, with upgrades and maintenance done for you. CloudMISP is always kept up to date with new versions of MISP, so your team will never miss out on value-adding new features and bug fixes.
January 2025
A reworked log search interface and performance and correlation improvements.
MISP v2.4.203 & v2.5.5 (Jan 12): Introduced a reworked log search interface with improved filtering, pagination, and added field details for easier auditing of system activity.
A new UI enhancement allows analysts to select object attributes via a checkbox directly in the event view, streamlining bulk attribute operations.
Multiple security fixes were included (e.g. stricter sanitisation of user edits and API key exposure in logs) to bolster platform security.
Support for the latest STIX converter was also integrated into testing tools, aiding the sharing and validation of threat data in STIX format.
MISP v2.4.204 & v2.5.6 (Jan 13): Focused on performance and correlation improvements. The attribute correlation engine was optimised by splitting lookups on value1/value2, resulting in faster correlation checks in MySQL.
Memory usage was reduced for Redis-based index queries, improving event index load times.
Threatmon community feed integration was added as well, giving users quick access to a new community threat feed out of the box.
February 2025
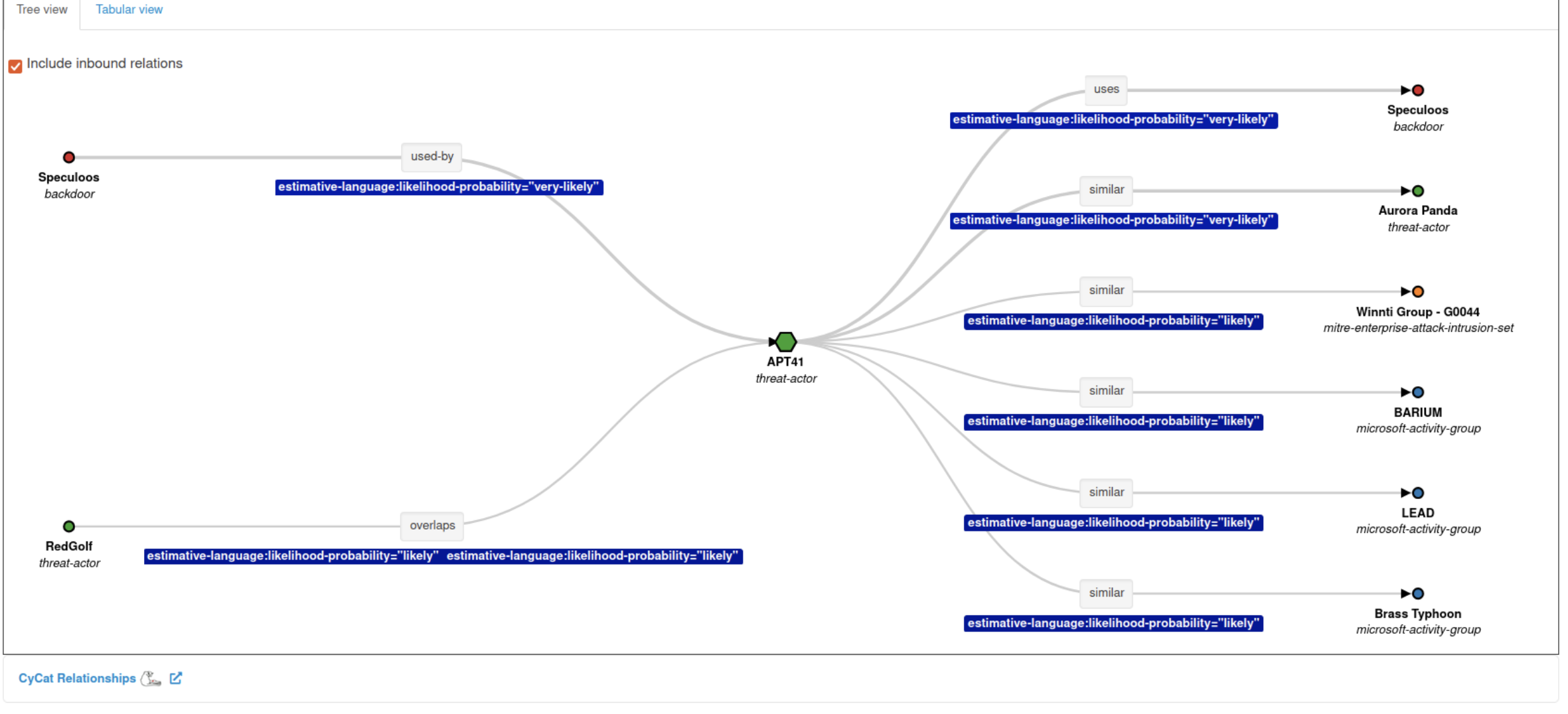
Over-correlation management, sync rules testing, flexible galaxy searches.
MISP v2.4.205 & v2.5.7 (Feb 24): Brought over-correlation management tools and sync improvements. A new “Quick Search for Overcorrelations” lets users identify and investigate attributes that correlate with an unusually large number of events, reducing noise from common indicators.
A Test Sync Rules widget was added to preview how many events would be shared under given synchronisation filters, giving analysts/admins visibility into data flows between instances.
Synchronisation filtering was improved by using organisation UUIDs (instead of names) for accuracy and by allowing rule-result previews. Frontend upgrades included updating the dashboard grid library (Gridstack) and the Markdown rendering engine, fixing UI bugs and ensuring dashboards and event descriptions render correctly.
Galaxy searches became more flexible by searching across additional cluster fields (not just synonyms), helping analysts find galaxy entities (threat actors, tools, etc.) more easily.
March 2025
Workflow automation modules, enhanced object relationship management, overhauled attribute search, upgraded background jobs.
MISP v2.4.206 & v2.5.8 (Mar 19): Delivered new workflow automation modules and search enhancements. Several workflow modules were added: for example, a module to filter events by tag (filter-tag), a “notify_user_toast” module to send in-app notifications, and a module to automatically create Analyst Notes. These let analysts set up custom alerting and tagging workflows, improving automation of repetitive tasks.
Object relationship management was enhanced – the UI now supports create/read/update/delete (CRUD) of relationship types and highlights them, making it easier to visualise and manage links between objects (e.g. indicating that an IP attribute “belongs-to” a certain network object).
Attribute search was overhauled: the search form was converted to use HTTP GET with query parameters (instead of complex session-stored criteria), enabling bookmarking and sharing of search URLs. Analysts can now easily download search results and the search behavior is consistent with the API (restSearch), with improved pagination and removal of duplicate endpoints.
Together, these changes mean more powerful on-demand querying and automation, boosting analyst efficiency in data triage.
MISP v2.4.207 & v2.5.9 (Mar 26): Focused on stability, background processing, and bug fixes. MISP’s background job system received a major update: test actions and other tasks in v2.5.9 now use the new SimpleBackgroundJobs (supervisor-based) framework instead of the legacy queue, with a default Supervisor config provided. This modernises how MISP runs background tasks (like correlations, imports), making them more reliable and easier to monitor – a boon for large workflows.
April 2025
Enhanced authentication plugin support for OIDC and LDAP, improved workflow editor UI.
MISP v2.4.208 & v2.5.10 (Apr 4): Authentication plugin support was enhanced: administrators can now enable OpenID Connect (OIDC) or LDAP authentication via configuration without manual code edits. (For example, OIDC plugins can be toggled in bootstrap.php as documented, and an option was added to safely escape LDAP filter characters.) These changes simplify enterprise single sign-on integration and prevent LDAP injection attacks.
Remote instance synchronisation got safer too – MISP will log a warning if a peer’s version is mismatched, alerting users to potential incompatibilities.
The workflow editor UI was refined: caching behavior for dropdown elements (like dynamic select boxes) was fixed so that editing complex workflows (with fields populated from URLs) is smoother and reflects the latest data.
Additionally, all core components (misp-STIX, objects, galaxies, warning lists) were updated to their latest versions, ensuring analysts have up-to-date classifications and mappings. Overall, April’s update hardened MISP’s security and improved the reliability of logins and workflow configuration – reducing disruptions in analyst workflows due to security or integration issues.
May 2025
Workflow engine enhancements, improved user management, better collections.
MISP v2.4.209 & v2.5.11 (May 7): Delivered major enhancements to the workflow engine, user management, and sharing logic. The workflow editor now allows running a debugged workflow on specific event IDs – meaning analysts can test and execute custom workflow actions on an event ad hoc, greatly aiding automation debugging.
Several workflow engine improvements arrived, such as a new _env context in Jinja templates (providing environment info like base_url for use in custom scripts) and support for overriding filtered/unfiltered modes in workflow tasks. These give power users more control when designing automation (e.g. conditional logic based on the MISP instance URL or toggling filter application).
Stateless workflow execution was improved and the UI for manually running workflows was refined for clarity. SSO enhancements: OpenID Connect (OIDC) login got more flexible by introducing identity-provider selection and a mixedAuth mode, allowing MISP to support multiple auth methods simultaneously (so users can choose between local login or different external IdPs – useful in federated environments).
New admin tools were added to the User module (e.g. userIP and IPUser utilities) to map users to IP addresses and vice versa, aiding in auditing and threat hunting (tracking which user may have seen or added an indicator from a given IP).
The collections feature (which groups objects or attributes) was improved: collections can now be viewed, edited, and deleted by UUID reference, making it easier to script and manage collections via the API or when UUIDs are known. Suricata IDS export underwent an initial refactor (laying groundwork for more robust rule export in future). Additionally, the database schema was tuned (event info field made case-insensitive) and audit log links for user actions were fixed. Importantly, this release fixed multiple stored XSS vulnerabilities (in the periodic email summary, sync rule creation page, and icon library views) reported during the 2025 hackathon.
By patching these, it eliminated avenues for malicious data to disrupt analyst browsers. It also adjusted sharing group and attribute behaviors – for instance, toggling an attribute’s correlation setting now properly marks the event as unpublished/modified to avoid unnoticed changes. Overall, v2.5.11 made automation more powerful and secure: analysts can automate tasks with greater nuance while the platform simultaneously closed security gaps that could affect daily usage.
MISP v2.4.210 & v2.5.12 (May 14): Brought UI and validation improvements crucial for analysis. In the event view, “Known Identifier” vs “False Positive” flags are now displayed in separate columns or indicators. This UI split helps analysts immediately distinguish between attributes that are actively marked as known good/benign versus those that are positively identified as malicious but false alarms – improving triage by clearly highlighting false positives independently of known safe indicators.
The event index page gained an option to display “extended” events (child events linked to others) inline, aiding analysts in quickly seeing if an event is part of a broader incident cluster without manual lookups.
Attribute validation was strengthened for vulnerability IDs: MISP now recognises and validates a wider range of vulnerability identifier formats (across all supported types). This ensures that when analysts add CVEs or other vulnerability tags, any typos or unsupported formats are caught, and context (like CVE descriptions via vulnerability lookup) is properly applied.
Under the hood, authentication was made more robust for mixed environments – issues with using multiple auth methods (e.g. TOTP 2FA + OIDC) together were fixed so route handling and user sessions load without conflict. A large number of security fixes landed: an external security audit by Second Nature Security reported numerous XSS and access issues – MISP 2.5.12 patched XSS vectors in server settings, user profile views, tag view pages, feed config, attribute replacement, Galaxy JSON output, and more. It also clarified a potentially dangerous config (download_attachments_on_load) in documentation due to its security implications.
Analyst “notes” tools were refined: the search filter in the Analyst Data index (which lists analyst notes/opinions) now works correctly, and organisation-scoped checks use stable UUIDs instead of numeric IDs for consistency. These fixes mean analysts can reliably filter and retrieve their collaborative notes. Additionally, the UI was cleaned up (hiding irrelevant “extending” columns when not needed, improving internationalisation strings).
With galaxy, object, and warning list libraries all updated to latest, this release solidified both the front-end experience and the data integrity, allowing analysts to work with more confidence in the correctness of the interface and the underlying data validations.
June 2025
Revamped search experience, API enhancements, usability improvements, correlation engine and performance enhancements.
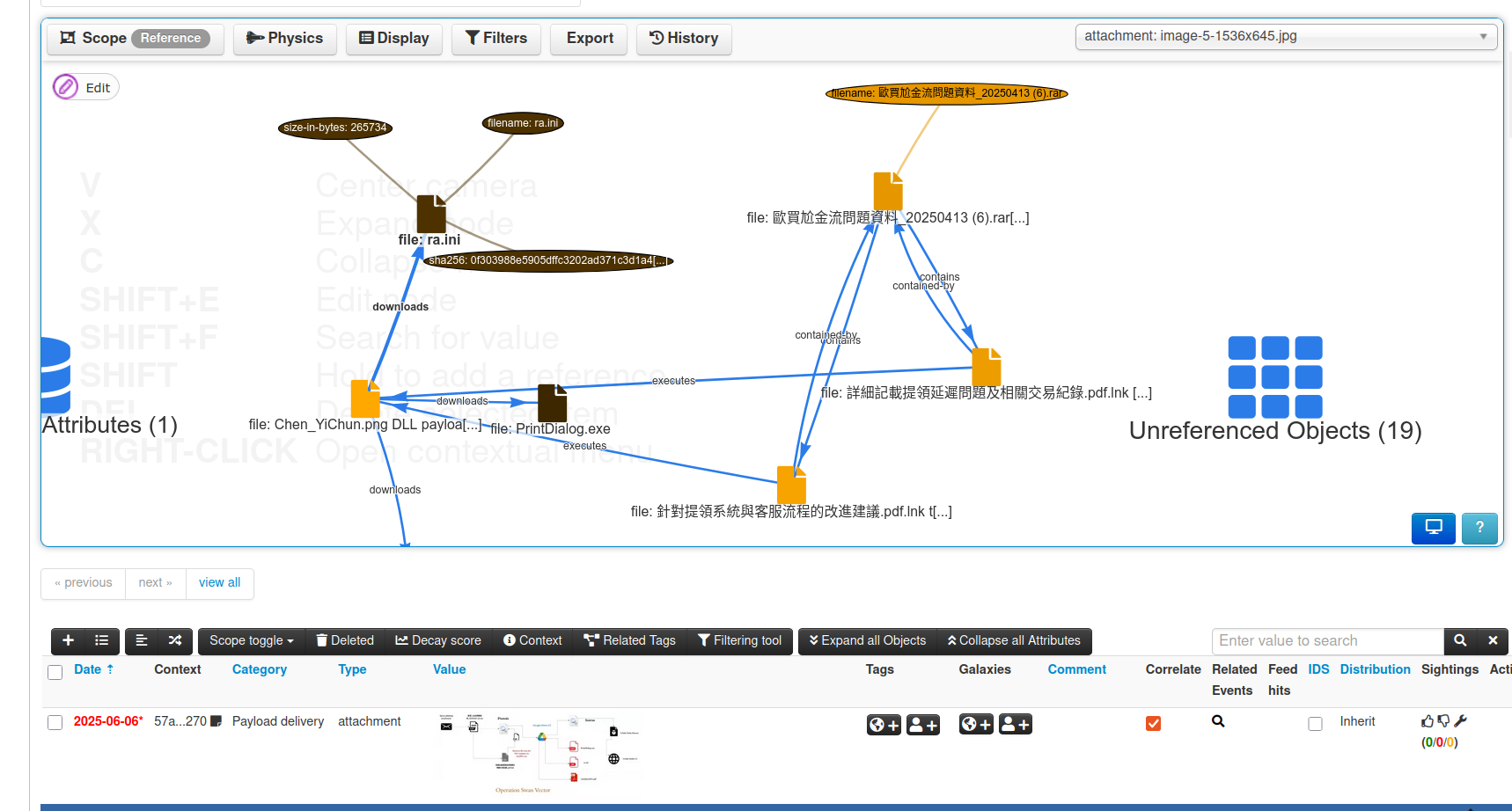
MISP v2.4.211 & v2.5.13 (June 6): A dual release focusing on critical security patches and a revamped search experience. The attribute search functionality was overhauled in response to prior limitations. Searches now use HTTP POST with a token-based system to handle query parameters. In practice, when an analyst runs a complex search (many parameters or long values), MISP will store the search criteria securely in Redis and return a token – this means even very elaborate queries no longer hit URL-length limits and pagination works flawlessly across multiple pages of results. An analyst can also have multiple search tabs open, each isolated by token, without interference. This “search-as-a-service” design greatly improves usability for threat hunters crafting complex filters.
API enhancements accompanied this: the REST API can now filter events by whether they extend another event or are extended by one (enabling queries like “show me base events vs. sub-events”). Similarly, the /attributes/search API gained the ability to filter by warning list status – e.g. one could exclude all indicators on a known-benign list, focusing only on potentially malicious IOCs, which is a huge time-saver for analysts doing data triage.
The API’s syntax was cleaned up (deprecating an old extend(ed) parameter in favor of clearer flags) and Accept headers can now dictate response format, making integration with other tools more flexible.
Several usability improvements landed: MISP now lets users attach files via the quick-add attribute form and guarantees that if you group attributes into an object, any file attachments remain intact. This prevents accidental data loss and encourages use of objects without the fear of “losing” evidence files. Galaxy cluster updates were improved – when a galaxy is updated, MISP now reassigns its local cluster IDs correctly to avoid sync inconsistencies (so all connected instances refer to the galaxy entry uniformly).
sThe Analyst Data view (for tracking an org’s notes/opinions) was cleaned up to show only relevant fields, decluttering the interface.
Also, event reports can be looked up by UUID now, meaning if an analyst knows a report’s UUID (from an alert or external system), they can directly retrieve it. All these changes in early June improved the efficiency of searching and data management, from faster queries to better API filters and fewer UI hiccups, directly benefiting analyst workflows in large instances.
MISP v2.4.213 & v2.5.15 (June 24): Brought significant correlation engine and performance enhancements, plus new UI features. The correlation exclusion engine was majorly reworked to function bi-directionally. Previously, correlation rules (to ignore certain patterns or values) only prevented new data from correlating against existing data. Now, with 2.5.15, if a rule says “do not correlate IP addresses from list X,” it will ensure that existing attributes also won’t correlate with newly added ones matching that rule. This consistency means analysts won’t see false correlations pop up simply because of entry order – it keeps unwanted correlations out of views entirely, reducing noise in correlation graphs. Additionally, filtering correlations by event info was fixed and some UI quirks in the correlation rule interface were polished.
On the performance side, database handlers were unified and queries optimised. The code handling “extended” events vs. “observer-extended” events was consolidated for efficiency. More noticeably, object-level searches (restSearch for objects) were sped up: the query planner now prioritises the event table and imposes sane limits on object lookups, drastically cutting CPU usage especially during large exports or complex object queries. Users on big instances will see faster object search results and less load during bulk exports.
New user-facing features were added as well: an “Import Choice” button now appears at the top of event view pages, giving a convenient way to import data (from file, galaxy, etc.) directly into an event without navigating away – this streamlines analysts’ workflow when enriching events. Administrators can now set role-based result limits for API queries, controlling how many results a given user role can pull per request. For example, an org could cap analysts to fetching 10k results via API to prevent accidental overloads – a useful safeguard for performance (though transparent to the analyst, it prevents runaway queries).
Search capabilities expanded: analysts can now filter attributes by their object relation field. This means in an event or attribute search, you could filter for attributes where object_relation = "domain" (for instance), retrieving all domain names regardless of which objects they belong to. This granular filter helps pinpoint specific kinds of indicators quickly across events. In the galaxy view, MISP now shows a count of attributes linked to each galaxy cluster. So if you open, say, the “APT28” threat actor galaxy, you immediately see how many attributes in your instance are tagged with that cluster – giving instant context of prevalence.
July 2025
Sweeping optimisations, Performance Toolkit, better logging and benchmarking capabilities, new OSINT feed.
MISP v2.5.16 & v2.4.214 (July 19): Dubbed “A Major Leap in Performance and Stability,” this release lived up to its name with sweeping optimisations. A standout addition is the Performance Toolkit accessible via cake Admin runDBScript. This console tool introduces new scripts (e.g. highPerformance) that apply advanced database indexes to events, attributes, objects, and correlations. By running these, admins can dramatically speed up search queries and correlation lookups at the cost of some extra disk and RAM usage (the documentation humorously warns not to run it on a “potato” server). For large MISP deployments, this means analysts experience much faster query response times once high-performance indexing is enabled – searching indicators or attributes across millions of records becomes far more efficient.
Under the hood, core query logic was refactored for speed: the attribute fetching mechanism was rewritten to use optimised SQL joins (including STRAIGHT_JOIN where applicable) instead of complex application logic. This change significantly reduces the latency when loading events and their attributes.
The correlation engine was also overhauled to eliminate performance-killing queries – it no longer uses expensive NOT IN() subqueries for de-correlation, instead leveraging temporary tables for speed. In fixing this, the team also resolved a bug that had caused overly aggressive removal of correlations; now correlation accuracy is maintained without the previous performance penalty.
Logging and benchmarking capabilities were improved: MISP can now output error logs in NDJSON format (newline-delimited JSON), which makes it easier to integrate with modern log management tools.
A new SQL Slow Query log UI was introduced, allowing admins (and power users) to list the slowest database queries through a web interface, filter them by controller/action, and even run EXPLAIN or ANALYZE on them with a single click. This is a boon for performance tuning – one can identify and troubleshoot bottlenecks without leaving MISP. Additionally, a function to purge old benchmark logs was added to keep things tidy, and error logs now include which user triggered an exception and the code location, speeding up debugging of issues.
On the community side, a new OSINT feed “Phishing.Database (phish.co.za)” was added to the default feed list, immediately providing users with a fresh source of phishing indicators to pull in. And of course, all the threat data catalogs (galaxies, objects, warning lists) were updated to their latest versions. In sum, July’s release significantly accelerated MISP’s performance for everyday use – large instances in particular will see snappier searches and correlation calculations – and introduced tools to keep it running optimally. For analysts, this means less time waiting on the system and more time analysing the actual intelligence.
August 2025
On-demand correlation and new Task Scheduler system.
MISP v2.5.18 (Aug 20): Introduced two notable features: the On-Demand Correlation Engine and a new Task Scheduler system. The on-demand correlation mode is an alternative correlation strategy that does not persist correlations in the database, but instead fetches correlation results live on the fly. This means when enabled, MISP will compute whether an attribute correlates with others at view-time rather than storing every correlation in a table. The advantages are immediate application of correlation rules (including retroactively) and faster event inserts with lower disk usage – there’s no need to run the background correlation job or worry about missed correlations due to a stuck worker. Essentially, if an analyst adds an indicator that should be excluded by a rule, it simply never shows a correlation, even with older data, because the check happens live. This feature can be transformative for instances with strict correlation filtering needs or storage constraints.
The brand-new Task Scheduler in MISP 2.5.18 gives administrators a built-in way to schedule recurring actions via the web UI. After enabling the Scheduler worker, a Tasks section becomes available in MISP where you can schedule periodic jobs (accessible at /tasks with proper setup). The scheduler supports automating common jobs like feed fetches and cache refreshes, server synchronisations (pulls/pushes), running ad-hoc workflow tasks, and generating periodic summary reports. For example, an admin can schedule “Fetch all feeds at 02:00 daily” or “Push my data to partner server every hour” directly in MISP, rather than using external cron jobs. Tasks can be run as specific users and have logs of their last run. This greatly improves workflow efficiency, ensuring analysts always have up-to-date data (feeds ingested overnight, etc.) and that routine maintenance tasks happen automatically.
In summary, August’s first release gave users powerful new automation tools: on-demand correlation for immediate, rule-respecting insights and a task scheduler to automate intelligence flows – all backed by a slew of fixes that keep the user experience smooth.
MISP v2.5.19 (Aug 20, released Aug 29): This follow-up release delivered important refinements to the features from 2.5.18 and additional bug fixes. On-Demand Correlation was improved with support for “top correlations” listing – meaning the UI can now display the most frequently correlated values even when using the on-demand engine. This helps analysts quickly spot which indicators are commonly appearing together, a useful insight for threat research, without having a full correlation table stored. Exception handling in the UI was made more user-friendly: if an error occurs, MISP will now direct the user to check the error log, rather than failing silently or giving an unclear message. The new Scheduled Tasks feature got quality improvements: scheduled tasks are now scoped to the user’s own organisation by default (preventing one org’s user from scheduling tasks for another org’s data) and when creating a task, the current user is pre-filled as the owner – this streamlines task setup and reinforces multi-tenant isolation. Furthermore, MISP now allows different worker config files per environment, which is helpful for administrators syncing configurations across dev/test/prod.
September 2025
Manual re-correlation of events and improved vulnerability matching.
MISP v2.5.21 (Sep 10): Brought a mix of new capabilities and maintenance fixes, especially around correlation and data updates. A key addition was the recorrelate event feature. For the first time, site admins can trigger a manual re-correlation of a specific event on demand (via the UI or an API endpoint /events/recorrelate/{id}). This is extremely useful if correlation rules were added or changed after an event’s creation, or if an admin suspects correlations might be outdated – one click and MISP will recompute that event’s correlations against all others. It reuses internal correlation logic (honoring rules) and ensures the event’s links are up-to-date without needing a full re-index job. For analysts, this means if something was missed or incorrectly correlated initially, an admin can fix it immediately, improving correlation accuracy in active investigations. There were also subtle UI improvements for correlation views: the “top correlations” panel (which shows commonly shared indicators) now indicates the correlation engine type being used, making it clearer whether results are from on-demand correlation or the traditional engine.
Vulnerability matching was improved – the AttributeValidation tool now supports more types of vulnerability IDs, broadening the scope of accepted formats when adding vuln attributes (so identifiers like e.g. GHSA or vendor-specific IDs might be recognised, not just CVEs). MISP’s threat data libraries were all updated (galaxies, objects, taxonomies), keeping the knowledge base current for analysts tagging and enriching data.
All in all, September’s release focused on making correlation maintenance easier and more precise (with on-demand recalc and better exclusion of no-corr events) and cleaning up various UI/UX issues that could inconvenience analysts. The platform became more predictable: what you mark to exclude stays excluded, what you expect to see on clicking a link is exactly shown, and new tools give admins the ability to keep correlation results accurate as MISP’s usage evolves.
October 2025
Event Report view improvements and indexing optimisations.
MISP v2.5.22 (Oct 2): Aimed at keeping MISP up-to-date and user-friendly with a batch of improvements and fixes. From an analyst’s perspective, a major UI improvement came in the Event Report view for extended events. Now, when viewing an event’s report, all child events of that event, as well as siblings (other children of the same parent event), are listed in the report view. This means if an event is part of a larger cluster (via the “extends event” relationship), an analyst reading its report can immediately see the other related events and navigate to them. It provides better context for incident report writing and pivoting, effectively consolidating a campaign’s related reports in one place.
Indexing optimisations were introduced for instances using the new high-performance indexes: if certain specialised indexes (on value1/value2) aren’t present, the system now handles it gracefully by falling back to a normal search approach. This prevents errors for those who haven’t run the performance indexing but still use value-based search filters.
MISP v2.5.23 (Oct 15): This update continued the trend of fine-tuning and bug squashing, while also introducing a couple of helpful features. A small but useful addition: events now include a field or flag indicating “first publication”.
November 2025
Speed improvements, new intel feeds, new UUID attribute type, improved JSON handling.
MISP v2.5.25 (Nov 16): Labeled a “Performance Update,” this release delivered speed improvements and new intel feeds. Most notably, it introduced significant performance optimisations for REST search queries.
New default feeds were added to MISP. This means out-of-the-box, MISP comes with additional OSINT feeds configured, providing more threat intelligence sources that analysts can enable with a click.
MISP v2.5.26 (Nov 20): Focused on performance improvements and interoperability fixes, with a couple of new features. It introduced data standardisation via a new “UUID” attribute type. This is a notable addition: attributes can now explicitly be of type “uuid”, which is useful for sharing or correlating objects by unique identifiers (for example, linking an indicator to an external system’s UUID or correlating sightings via UUIDs). By treating UUIDs as a first-class attribute type, MISP can apply proper formatting, validation, and perhaps correlation logic (maybe recognising when a UUID corresponds to an internal object). This helps analysts cross-reference with other databases/tools that use UUIDs.
For an analyst, this release improves consistency and integration: using UUID attributes can reduce ambiguity when correlating with external info, and overall system snappiness and reliability were further enhanced.
December 2025
Improved support for "Meta Communities", foundational Beta UI/UX mode, new workflow modules.
In December, MISP released versions 2.5.29 and 2.5.30 together, delivering a significant set of UI/UX updates, new workflow modules, and improvements to core analyst workflows while maintaining a strong focus on security and data integrity.
For analysts, the most visible change was the introduction of an opt-in Beta UI/UX mode contributed by Cosive's own Chris Horsley, our co-founder and CTO. This beta interface reorganises major parts of the user experience:
- The Event Index was redesigned with a more responsive layout, clearer columns, humanised timestamps, and a centralised action dropdown, making it easier to scan and act on events at a glance.
- Navigation was refreshed with a restructured top bar and improved menu flows, helping analysts move quickly between modules without hunting through dense menus.
- Organisation logos in the Event Index now load via a dedicated cached endpoint instead of inline base64 images, resulting in faster page loads especially on instances with many organisations.
Alongside the UI work, December’s releases added new workflow automation modules to extend analyst efficiency:
- A module that tags events based on MaxMind DB data (helping enrich with geolocation/ISP context), and
- A module that automatically adds tags using external vulnerability intelligence from vulnerability.circl.lu, helping surface vulnerability context without manual lookup.
Behind the scenes, schema and library updates (e.g., updated warning lists) ensured analysts had the latest threat classifications available for tagging and enrichment. Various parts of the REST API were tightened — including filters for org_id and orgc_id — allowing more precise API-driven searches.
A series of bug fixes improved day-to-day work:
- Long
value2fields no longer break event viewing in on-demand correlation, - IPv4/IPv6 mapping issues were fixed in correlation, and
- The dashboard “Add” widget was stabilised.
Security remained a priority with multiple CVE-level fixes and XSS regressions addressed (including fixes for issues exposed during sharing-group edits and malicious external_baseurl cases), ensuring analysts can safely view and interact with shared data.
Impact on analyst workflows:
- The Beta UI makes large-scale event triage and navigation faster and less error-prone.
- New automation modules reduce repetitive enrichment steps.
- API refinements and structured filters make scripted workflows (e.g., SIEM ingestion or automation playbooks) more reliable.
- Security hardening increases confidence when reviewing community-shared indicators.
MISP v2.5.31 (Dec 23, 2025): The final release of 2025 focused on polish, synchronisation reliability, and ensuring the knowledge base was up-to-date for the year ahead, rounding off the major work of the year.
This update refreshed MISP’s core threat libraries — including taxonomies, galaxies, object templates, and warning lists — bringing in all late-2025 updates. Analysts benefit immediately from having the newest threat actor clusters, tool families, data classifications, and common indicator lists baked into the system without needing manual imports.
On the interface side, a series of UI refinements were applied to elements of the existing and beta UI. These were targeted adjustments to address feedback from everyday use: layout tweaks, clearer labelling in dropdowns and buttons, and smoother responsiveness in core screens such as event view and indexing. The result is a slightly clearer, less fiddly experience when performing common tasks like reviewing events, adding attributes, or navigating between related content.
Synchronisation behaviour saw practical improvements that reduce friction in federated sharing setups:
- Sync jobs handle conflict conditions more gracefully,
- Expanded checks help ensure that events and objects propagate fully between peers, and
- Edge cases that could previously cause stalls during high-volume syncs are now resolved.
Although 2.5.31 did not introduce headline-grabbing features, it bundled a series of important fixes and backend refinements to ongoing capabilities introduced earlier in 2025 — such as correlation logic, rapid search performance, scheduler stability, and REST API consistency — helping stabilise those workflows as adoption of new features matured.
Impact on analyst workflows:
- Analysts start 2026 with fresh threat knowledge built into MISP’s classification layers, reducing the need to manually update threat libraries.
- Everyday interface tasks feel smoother and less distracting.
- Data synchronisation across instances is more reliable, reducing the need for manual interventions during collaborative CTI operations.
- Stability fixes ensure that automation features introduced throughout 2025 continue to behave predictably in production.
Thank You to the MISP Team
Looking back, 2025 has truly been an impressive year for MISP. The platform is more user-friendly, more powerful, and more robust than ever – all thanks to the dedication of the MISP core developers and the wider community who contribute time and expertise. The MISP team themselves noted how far things have come, extending a warm thank-you to all the contributors, users, analysts, operators, and supporters who made this year so successful.
On behalf of Cosive and the many threat intelligence teams who rely on MISP daily, we want to echo that sentiment. Thank you to the MISP project leads (Andras Iklody, Alexandre Dulaunoy and team) and to every volunteer, developer, and researcher who helped improve MISP in 2025. Your hard work – from coding new features to patching bugs and updating intel libraries – directly empowers the global security community to share and act on threat information faster and more effectively.
We’re proud to be part of this community (and humbled that we could contribute a little to MISP’s evolution this year). Here’s to an even stronger 2026 – the MISP website is already hinting at exciting new services and evolutions on the horizon, including the NGSOTI initiative, and we can’t wait to see them come to fruition.

