Your SOC is drowning in alerts.
Your SOC analysts face an endless flood of unstructured, unverified, and unactionable alert leading to:
- Alert fatigue and burnout
- Slower response times to real threats
- Underperformance relative to investment in tools and people
This all adds up to: missed signals, siloed teams and systems, and avoidable risk.
The Modern SOC has one key advantage.
The typical SOC underperforms because it is fragmented, chaotic, reactive, and drowning in noise.
A Modern SOC is unified, intelligence-driven and automated, freeing analysts to focus on high-impact investigation and response.
Threat intelligence is the difference: it empowers the Modern SOC to focus clearly on the most important threats.

The Modern SOC is fuelled by threat-informed defence.
Threat intelligence turns noise into knowledge, so you can:
• Understand who’s targeting you, why, and how
• Prioritise vulnerabilities that actually matter
• Replace noise with signal in your SOC
Threat intelligence improves leadership decision-making.
Threat intelligence isn’t just for analysts. Threat intelligence briefings give security leaders the clarity to prioritise effort and investment where it reduces the most risk for every dollar spent.
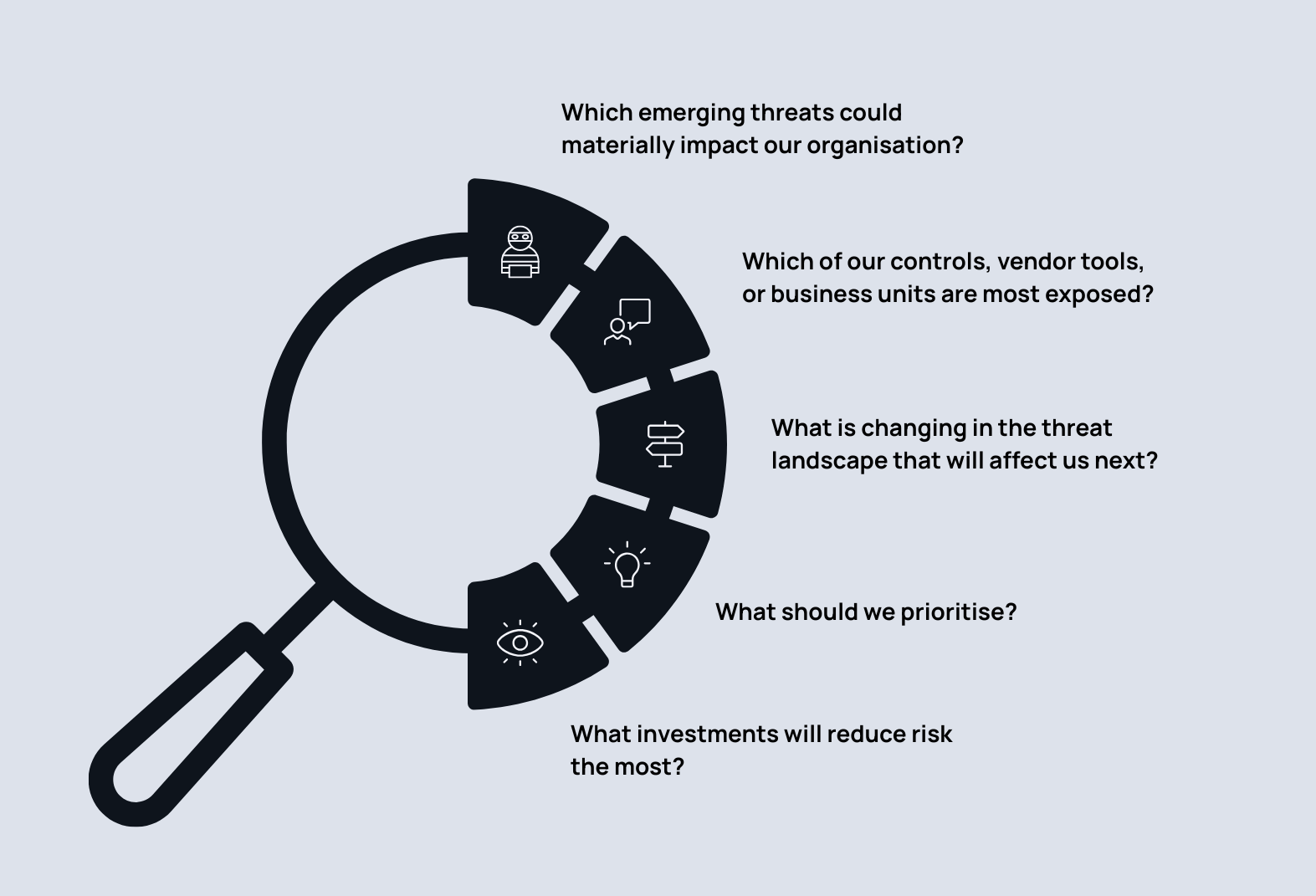
From strategy to execution: meet Cosive
We've helped government agencies and private organisations across APAC and the globe to modernise their SOC since our founding in 2015.

We are APAC's threat intelligence leaders
The Australian Signals Directorate entrusted Cosive to play a pivotal role in designing and engineering the CTIS program, Australia’s national cyber threat–sharing initiative.
Our team led major national intelligence–sharing initiatives at AusCERT, JPCERT, and the New Zealand Internet Task Force (NZITF), strengthening collaboration and capability across the region.

Advancing threat intelligence practice across the globe
Cosive’s experts are core contributors to the global threat intelligence ecosystem. We've helped shape key technical standards such as STIX, TAXII, MISP, and are collaborators on the CTI-CMM framework, the world's leading cyber threat intelligence maturity model.
We continue to advance threat intelligence globally through workshops and keynote presentations at leading industry events, including FIRST, AISA CyberCon, and NZITF.
We deliver outcomes
Our expertise is transforming threat intelligence strategy into operational reality.

CloudMISP - Cosive's Managed Threat Intelligence Platform
CloudMISP is a fully managed service that simplifies the collection, enrichment, and distribution of threat intelligence for the Modern SOC. It removes the need for internal maintenance or specialist resources by providing a secure, expertly operated platform.
The result is faster deployment, lower overhead, and confidence in a best-practice, enterprise-grade solution.

Threat Intelligence Maturity Assessments
Our Threat Intelligence Maturity Assessment Service evaluates your progress toward achieving a Modern SOC in a structured, measurable way.
Using the CTI Capability Maturity Model (CTI-CMM) as its foundation, the assessment benchmarks current intelligence practices against globally recognised standards across people, processes, and technology, and charts a course for improvement.
Our threat intelligence leadership team

Chris Horsley, CTO & Cofounder
Global speaker and trainer on threat intelligence best practices, including at major security conferences including FIRST, AusCERT, AISA CyberCon, and hack.lu.

Terry MacDonald, COO & Cofounder
Chairperson of the New Zealand Internet Task Force, leading efforts to strengthen national cybersecurity collaboration. Key contributor to international threat intelligence standards (STIX, TAXII, and CybOX).

Prescott Pym, Principal Consultant
Helped design and launch Australia’s national cyber threat intelligence sharing program (CTIS), led by the Australian Signals Directorate. 14 years Security Operations at Verizon.

Joe Cozzupoli, Field CISO & Principal Security Advisor
Focused on helping clients operationalise threat intelligence and Security Operations to reduce risk and deliver measurable business outcomes. Over 20 years in cyber security.


